Types of Threat Intelligence: Why Most Teams Fail
Threat Intelligence Credential Security Dark Web Monitoring Best Practices
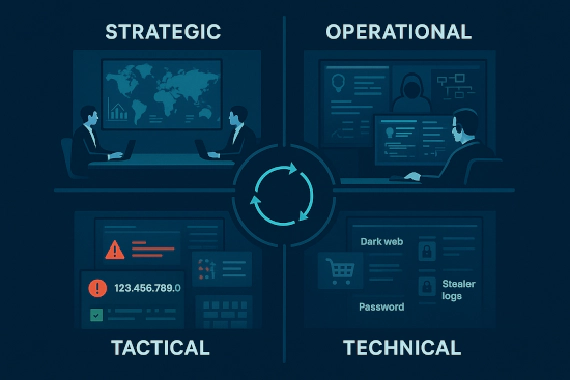
What Are the Types of Threat Intelligence? There are four types of threat intelligence, and most organizations are …

Threat Intelligence Credential Security Dark Web Monitoring Best Practices
What Are the Types of Threat Intelligence? There are four types of threat intelligence, and most organizations are …

Threat Intelligence Dark Web Monitoring Best Practices Credential Security
What Is the Threat Intelligence Lifecycle? The threat intelligence lifecycle is a six-phase framework that security …

Dark Web Monitoring Threat Intelligence Best Practices
How is threat intelligence collected? Threat intelligence collection isn’t some magical process where data just appears …
Dark Web Monitoring Best Practices
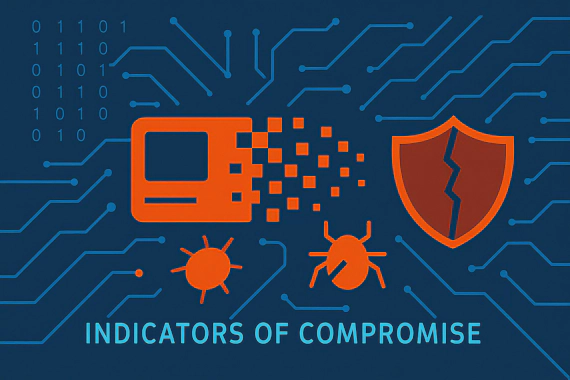
What Are Indicators of Compromise (IOCs)? Indicators of Compromise (IOCs) are digital clues that attackers leave behind …

Dark Web Monitoring Threat Intelligence Best Practices
What is Threat Intelligence Management? If you’ve been in security for any length of time, you’ve probably been drowning …

Dark Web Monitoring Threat Intelligence Best Practices
What is a Cyber Threat Monitoring Tool? A cyber threat monitoring tool alerts security teams to potential threats before …

Dark Web Monitoring Threat Intelligence Best Practices
What Are Threat Intelligence Tools? Threat intelligence tools provide security teams with information about potential or …

Cyber Threat Intelligence Dark Web Monitoring
Cyber Threat Intelligence Explained Cyber Threat Intelligence (CTI) is the process of collecting, analyzing, and sharing …

What is shadow IT and why is it a problem? Shadow IT refers to software that employees use for work without the …

What are the Risks of Shadow IT When it comes to Shadow IT, there are five primary risks that it introduces into …

What is a data breach? A data breach is a security incident that enables unauthorized access to sensitive information. …

Initial Response (First 24 Hours) During the first 24 hours after identifying a breach, security teams need to identify …