
Data Risk Management: Framework, Assessment & Strategies
Risk Management Data Security Best Practices
What is data risk management? Every company has data worth stealing. The question is whether you know where it is and …

Learn how to prevent catastrophic breaches like Equifax by understanding what went wrong.
• Attackers exploited an unpatched Apache Struts vulnerability and an expired security certificate to steal 147.9 million records over two months undetected.
• Chinese military attackers likely orchestrated the attack to build intelligence dossiers on U.S. citizens and government officials.
• The breach cost Equifax $1.38 billion in settlements and mandatory security improvements while destroying executive careers.
• Basic security failures caused this breach. Patch management and certificate renewals would have stopped it. So would network segmentation.
In 2017, Equifax suffered a data breach that exposed the personal information of 147.9 million Americans. That’s roughly 40% of the U.S. population.
The attackers exploited a known vulnerability that had a patch available for months. They remained undetected for 78 days because an SSL certificate had expired and nobody noticed. When Equifax finally discovered the intrusion, executives sold stock before going public.
The Equifax breach became a case study in how basic security failures led to catastrophic outcomes. Every failure was preventable with standard practices.
This analysis covers exactly how the attack unfolded and what security teams can learn to prevent similar breaches.
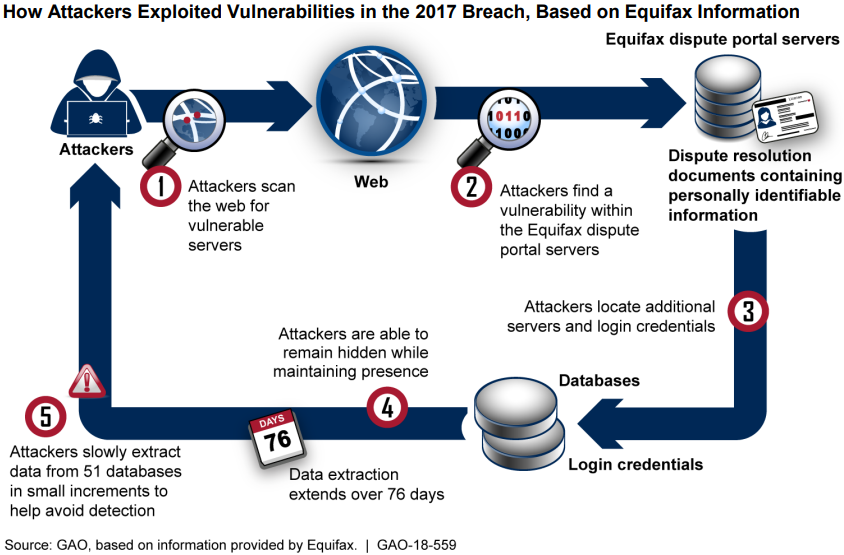
The Equifax breach started with a web application vulnerability that had been public knowledge for months.
A data breach occurs when attackers gain unauthorized access to systems and steal sensitive information. Unlike data leaks from misconfigurations, breaches require attackers to actively exploit vulnerabilities to access protected systems.
On March 7, 2017, Apache disclosed CVE-2017-5638, a critical vulnerability in the Apache Struts web framework. The flaw allowed remote code execution through a malicious HTTP Content-Type header. Apache released a patch the same day.
Three days later, on March 10, attackers exploited this exact vulnerability on Equifax’s online dispute portal. The company’s security team received alerts about the patch but failed to apply it across all systems.
For the next two months, the attackers moved laterally through Equifax’s network. They found plaintext credentials stored on internal systems. These credentials gave them access to databases containing consumer financial records.
Between May and July 2017, the attackers exfiltrated data on 147.9 million people. They encrypted the stolen data to avoid detection by network monitoring tools.
Here’s why they got away with it for so long.
Equifax had network monitoring tools designed to detect exactly this type of data exfiltration. The tools were supposed to decrypt and inspect traffic leaving the network.
They weren’t working.
A critical SSL certificate had expired in January 2017. Without a valid certificate, the monitoring tools couldn’t decrypt traffic. The attackers’ encrypted exfiltration looked like normal HTTPS traffic.
Nobody noticed the expired certificate for over six months.
On July 29, 2017, administrators finally renewed the certificate. The monitoring tools immediately flagged suspicious activity. By then, the attackers had been inside for 78 days and stolen data on 40% of U.S. adults.
The GAO investigation report documented these failures in detail. Equifax had security tools but failed to maintain them.
This is where the Equifax breach gets interesting. The stolen data never showed up on dark web markets. That’s unusual for a financially motivated attack.
Attribution is the process of identifying who conducted a cyberattack based on technical evidence and attack patterns. Nation-state attackers typically don’t sell stolen data because their goal is intelligence gathering, not profit.
On February 10, 2020, the U.S. Department of Justice charged four members of China’s People’s Liberation Army with the Equifax hack. The indictment named Wu Zhiyong, Wang Qian, Xu Ke, and Liu Lei from PLA Unit 54398.
The evidence suggests Equifax was part of a broader Chinese intelligence operation. The 2015 Office of Personnel Management breach exposed 22 million federal employee records. The 2018 Marriott breach exposed 500 million hotel guest records. Neither dataset appeared on dark web markets.
Investigators believe China combined these datasets to build dossiers on U.S. government officials and intelligence officers. Financial records from Equifax reveal who has money problems and might be vulnerable to recruitment or blackmail.
The attackers were patient. They gained initial access in March but waited until May to begin data exfiltration. This patience is typical of nation-state operations focused on intelligence gathering rather than quick financial gain.
The Equifax breach hit the company from every angle.
The total cost of the breach reached $1.38 billion. This included:
Settlement costs: Equifax agreed to pay up to $700 million to settle with the FTC, CFPB, and 50 state attorneys general. The fund included $425 million for consumer compensation.
Security improvements: The settlement required Equifax to spend $1 billion improving its information security practices over five years.
Insurance recovery: Equifax had $125 million in cybersecurity insurance coverage, which it collected in full.
Stock impact: Equifax shares dropped 35% in the week following disclosure. The company’s market cap fell by $5 billion.
The breach ended multiple careers at Equifax:
The breach triggered new requirements for credit bureaus:
For the 147 million affected individuals:
Here’s exactly when each event occurred and how the attack progressed.
| Date | Event |
|---|---|
| March 7, 2017 | Apache discloses CVE-2017-5638 and releases patch |
| March 10, 2017 | Attackers exploit vulnerability on Equifax dispute portal |
| May 13, 2017 | Attackers begin lateral movement and data exfiltration |
| July 29, 2017 | Expired SSL certificate renewed, suspicious activity detected |
| July 30, 2017 | Equifax takes their dispute portal offline |
| August 2017 | Multiple executives sell company stock |
| September 7, 2017 | Equifax publicly discloses the breach |
| September 26, 2017 | CEO Richard Smith resigns |
| February 10, 2020 | DOJ indicts four Chinese military officers |
The 78-day detection gap matters. The average time to identify a breach is 207 days. Equifax was faster than average but still gave attackers nearly three months of access.
Equifax’s incident response became a case study in what not to do.
Confusing websites: Equifax created equifaxsecurity2017.com to help affected consumers. The domain looked like a phishing site. Their social media team accidentally directed people to securityequifax2017.com, a parody site.
Waiving legal rights: The original terms on the response website required consumers to waive their right to sue in exchange for checking if they were affected. Equifax removed this after public backlash.
Executive stock sales: Several executives sold shares between learning about the breach and the public announcement. Only one was charged with insider trading.
Delayed notification: Equifax discovered the breach on July 29 but waited until September 7 to disclose it, a 40-day gap.
The FTC settlement website now handles consumer claims, not Equifax.
The Equifax breach was entirely preventable. Here’s what security teams should take away.
CVE-2017-5638 had a patch available for two months before the attack. Equifax’s security team was aware of it but didn’t apply it to all systems.
What to do differently:
Equifax had the right monitoring tools. They just weren’t working because of an expired certificate.
What to do differently:
Once attackers got inside, they moved freely through the network. Credentials found on one system gave access to many others.
What to do differently:
The attackers used legitimate credentials to access sensitive databases. The systems had no way to distinguish between authorized and unauthorized use.
What to do differently:
Attackers found plaintext credentials on internal systems after getting in. Those credentials unlocked access to sensitive databases.
What to do differently:
The Equifax breach ranks among the largest data breach examples in history.
By records exposed: Yahoo (3 billion), First American (885 million), and Marriott (500 million) exposed more records. But Equifax exposed Social Security numbers and financial data, making each record more damaging.
By financial impact: The $1.38 billion cost exceeds most breach settlements. Only the Capital One breach ($190 million fine plus remediation) and Yahoo ($117.5 million settlement) approach this scale.
By systemic importance: Equifax is one of three major credit bureaus. Unlike a retailer breach, consumers can’t choose to stop doing business with Equifax. The company has your data whether you want them to or not.
The breach shares common elements with other major incidents. Like the Target breach, attackers exploited vendor relationships and moved laterally through insufficiently segmented subnets. Like many breaches, basic security hygiene failures made this attack possible.
The Equifax breach succeeded because of multiple preventable failures. Here’s how to avoid the same fate.
Treat vulnerability management as critical infrastructure. Don’t just track patches, verify they’re applied. Run regular vulnerability scans and treat unpatched critical systems as incidents.
Monitor your monitoring. Security tools only work when they’re functioning. Build dashboards that show tool health, not just threat detections. Alert on monitoring gaps.
Assume a breach in your architecture. Design networks expecting attackers will get in. Segment sensitive systems. Monitor for lateral movement.
Watch for your credentials on the dark web. Attackers often obtain credentials from previous breaches before launching new attacks. Dark web monitoring detects exposed credentials so you can reset them before attackers exploit them.
Practice incident response. Equifax’s response made a bad situation worse. Run tabletop exercises. Have pre-approved communication templates. Know who makes decisions before a crisis hits.
The Equifax breach shows what happens when credentials aren’t protected. Attackers who get inside your network will hunt for credentials to expand their access.
Many attacks start with credentials leaked in previous breaches. Employees reuse passwords, and attackers exploit that. Breachsense monitors dark web markets and hacker forums for your organization’s credentials. When employee passwords appear in new breaches, you can reset them before attackers try using them.
Book a demo to see how credential monitoring fits into a layered security approach.
Attackers exploited an unpatched Apache Struts vulnerability (CVE-2017-5638) to access Equifax systems in March 2017. They moved laterally through the network and stole data on 147 million Americans over 78 days. The breach went undetected because an expired SSL certificate disabled network monitoring. Equifax disclosed the breach in September 2017.
Yes. Every failure that enabled this breach was preventable with standard security practices. Patching the Apache Struts vulnerability would have blocked initial access. Renewing the expired SSL certificate would have caught the exfiltration. Network segmentation would have limited lateral movement. None of these required advanced tools.
Most claimants who opted for cash received only $5-20, not the advertised $125. This happened because 4.5 million people filed claims against a capped $31 million fund. The settlement prioritized credit monitoring services over cash payments.
The U.S. Department of Justice indicted four members of China’s military (PLA Unit 54398) for the attack in February 2020. The stolen data never appeared on dark web markets, suggesting the attack was for intelligence gathering rather than financial gain.
CVE-2017-5638, a remote code execution vulnerability in Apache Struts. The flaw allowed attackers to execute commands via a malicious HTTP header. A patch was available two months before the breach, but Equifax hadn’t applied it.
78 days. Attackers gained initial access on March 10, 2017, and weren’t discovered until July 29, 2017. An expired SSL certificate disabled Equifax’s network monitoring tools, giving attackers free rein to exfiltrate data.
The attackers stole Social Security numbers, birth dates, and addresses. Around 200,000 people also had credit card numbers exposed. Some UK and Canadian residents were affected too.

Risk Management Data Security Best Practices
What is data risk management? Every company has data worth stealing. The question is whether you know where it is and …

Authentication Dark Web Monitoring Credential Monitoring Security Tools
Top 10 Account Takeover Solutions at a Glance Platform Category Best For Breachsense Credential Intelligence Dark web …