- Early threat detection
- Improved incident response
- Prevent ransomware attacks
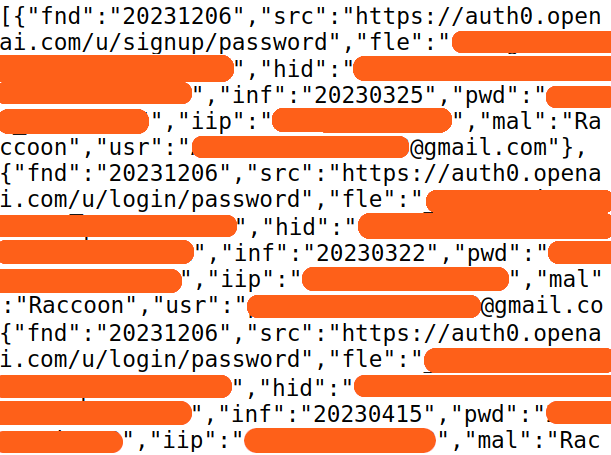
- Search open source intelligence
- Comprehensive threat visibility
- Power incident response investigations
- Prevent risks due to third-party breaches
- Gain visibility into threat actors discussing your organization
- Attack surface management enables you to secure shadow IT
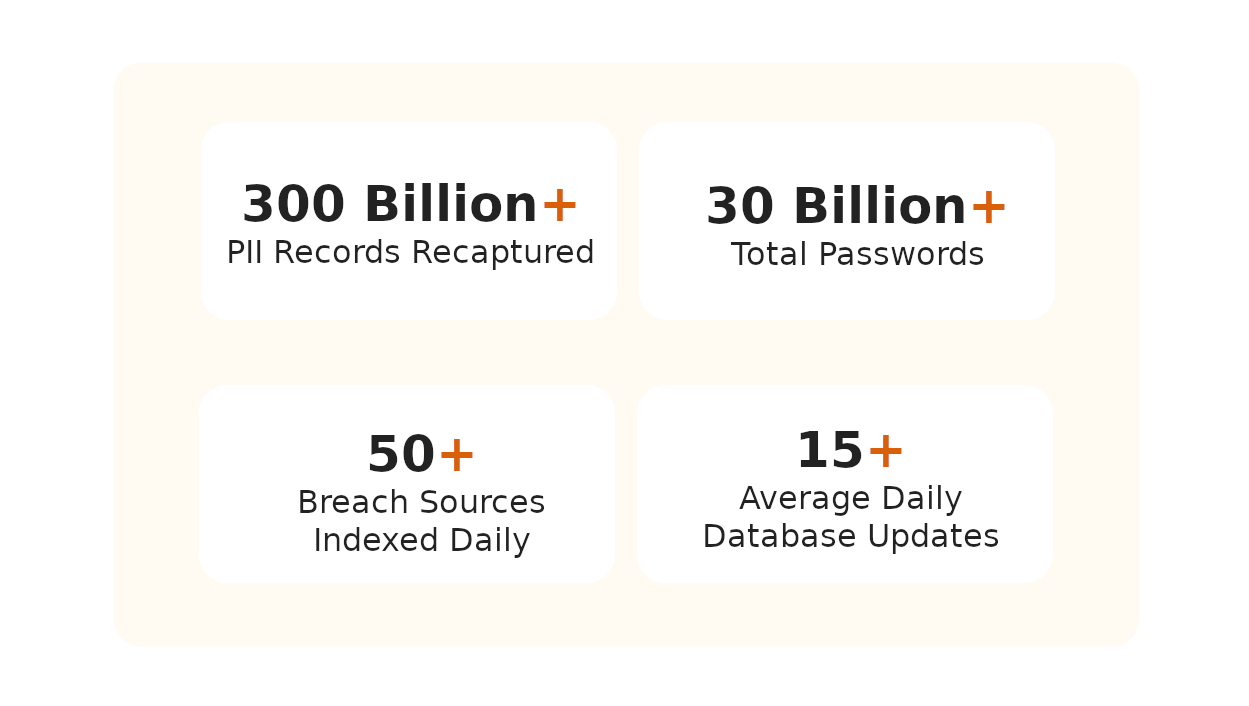
An API-driven breach detection platform that enables:
Stop the most complex attacks
Accelerate incident response times
Maximize your resources
Trusted by great companies from all over the world
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
Breachsense Is Perfect For
Penetration Testers
Red Teams
Enterprise Security Teams
Incident Response Analysts
M&A Research
Frequently Asked Questions
What is breach protection?
Breach protection is essentially a security system that protects your organization’s sensitive data from unauthorized access. It works by continuously monitoring the dark web for leaked credentials, customer information, and proprietary data. A breach protection platform will alert you instantly if your data appears in a new breaches.
How do I know if my data was breached?
Data breaches can be detected through multiple channels. Security teams can identify potential breaches through system logs showing unauthorized access, unusual data transfers, or suspicious authentication patterns. External notifications may come from law enforcement, security researchers, threat intelligence partners, or industry CERTs when your data is discovered in unauthorized locations. Regular security audits and automated monitoring tools provide additional detection capabilities. By identifying breached data early, you can mitigate the impact before the data is exploited.
What is the most common source of data breaches?
While attackers use many techniques to break into organizations, compromised credentials remain the primary attack vector. According to Verizon, 86% of data breaches exploit weak or stolen credentials. Having continuous visibility into your organization’s exposed credentials allows security teams to reset leaked credentials before they get exploited.
How do companies prevent data breaches?
Organizations prevent data breaches through a combination of technical controls and security best practices. Core defenses include multi-factor authentication (MFA), password managers, and network segmentation to contain potential compromises. Security teams complement these controls with continuous dark web monitoring to detect leaked credentials and session tokens before they’re exploited. Regular penetration testing and assumed breach exercises help identify and address vulnerabilities before attackers exploit them.