What causes data breaches?
The average cost of a breach is USD 4.45 million
86% of breaches leverage stolen credentials
Instant Alerts for Quick Incident Response
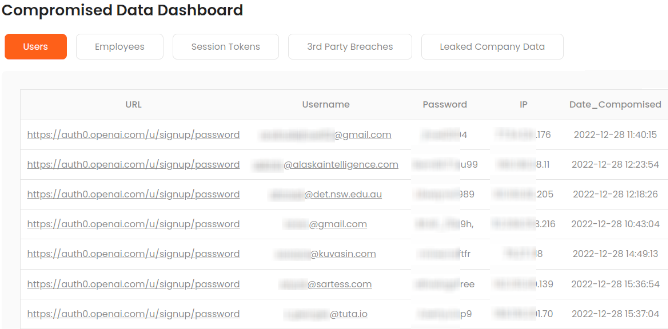
Gain visibility into the dark web and leverage actionable threat intel to quickly locate your breached data
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
Breachsense Is Perfect For
Penetration Testers
Red Teams
Enterprise Security Teams
Incident Response Analysts
M&A Research
Frequently Asked Questions
What is data breach monitoring?
Data breach monitoring is the process of monitoring the open, dark, and deep web to uncover data breaches within your organization. Continuous data breach monitoring ensures that if a data breach does occur, your security team will be able to respond immediately.
MORE INFO: What is a data breach?
MORE INFO: What is data breach monitoring?
Where can I check if my data has been breached?
Breachsense allows you to search across multiple data breaches, infostealer logs, and combo lists to see if your data has been breached. Use the Breachsense dark web scanner to see which of your organization’s accounts have been compromised.
How do you detect a data breach?
Detecting a data breach requires continuous monitoring across a broad range of sources, like the dark web, hacker forums, and ransomware channels, for compromised data. By tracking leaked credentials, stolen company data, and patterns of unusual activity, organizations can identify breaches early.
What tools are used to identify breaches?
A number of common tools that are used include IDS, SIEM, UEBA, EDR and data breach detection software. Each of these tools plays an important role and should be used in combination to help protect your organization from data breaches.
How are data breaches detected?
Data breaches are often detected through a combination of monitoring tools, breach detection tools, anomaly detection algorithms, and regular security audits. Data breach monitoring services continuously scan various sources such as the dark web, hacker forums, and Telegram for leaked data. When monitored assets are found in leaked data or unusual patterns of network traffic are detected, alerts are generated for further investigation to confirm and respond to potential breaches.
What techniques are used to detect a breach?
Network traffic analysis, intrusion detection systems (IDS), SIEM data, log analysis, EDR tools and data breach monitoring are often used. These methods help identify unusual patterns, unauthorized access or actual leaked data. Additionally, regular security audits, vulnerability scanning, and penetration testing can uncover vulnerabilities that can lead to a breach.
How does data breach detection software prevent cybercrime?
By detecting data breaches in real time, your security team will be able to react immediately before any damage is done. The moment a breach is detected, you can:
- Disable Compromised Accounts
- Prevent Fraudulent Purchases
- Upgrade Your Security Measures








