- Breachsense tracks all layers of the darknet continuously, including Tor websites, private IRC and Telegram channels, ransomware threat actors, cybercrime communities and forums, and more.
- Breachsense will notify you whenever it detects your employees’, customers’, or software suppliers’ usernames or passwords as well as any other relevant sensitive data on dark web marketplaces.
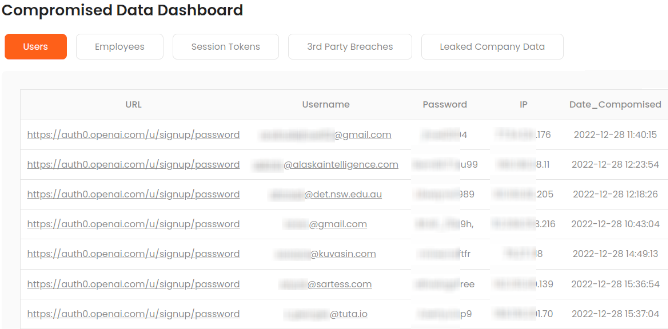
- Detect leaked credentials, session tokens, sensitive company data and upcoming attacks related to your organization to prevent attacks before they happen.
How Breachsense Monitors Data Breaches for You
Early Data Breach Detection and Response
Easy Integration with Your CTI Toolset
Instant Alerts for Quick Incident Response
Boost Your Cyber Security with the #1 Data Breach Monitoring Platform Trusted by Great Companies from All Over the World
Our team uses Breachsense data to gain initial access during pen testing and red team engagements. The API is simple to use and the support is always helpful and responds quickly.
Our Security Colony platform relies on Breachsense data as part of our dark web monitoring service. The data is continuously updated and high quality. Highly recommend!
We rely on Breachsense for a lot of data. Their frequent database updates, constant availability, and handling of big and small breaches alike means we are always covered.
Breachsense Is Perfect For
Penetration Testers
Red Teams
Enterprise Security Teams
Incident Response Analysts
M&A Research
Frequently Asked Questions
What is Data Breach Monitoring?
Data breach monitoring is the process of monitoring data breaches for mentions of specific individuals, brands, phone numbers, and other types of sensitive information. With data breaches becoming increasingly common, leveraging a data breach tool for monitoring your assets is crucial for protecting your customers’ and employees’ sensitive information.
How Does Data Breach Monitoring Work?
Breachsense continuously tracks millions of online sources, including IRC and Telegram channels, private cybercrime communities, ransomware marketplaces, and more. Your security team is notified the moment there are any mentions of your:
- Employee or customer account credentials or other sensitive data
- Login credentials to your C-level executive accounts
- Credentials for remote access servers like SSH, Remote Desktop, and FTP
- Internal company emails or documents
- Employee corporate or government-issued IDs
How Data Breach Monitoring Helps Prevent Cybercrime?
By detecting data breaches in real time, your security team will be able to react immediately before any damage is done. The moment a breach is detected, you can:
- Reset Compromised Passwords
- Terminate Compromised Sessions
- Prevent Fraudulent Purchases
- Upgrade Your Security Measures
Is A Data Breach The same As A Data Leak?
It’s true that both terms - “data breach” and “data leak” - seem as if they referred to the same type of a cyber threat. In reality, however, they do have slightly different meanings. A data breach occurs where a third party gains unauthorized access, often malicious, to compromise sensitive information within a system or network. A data leak, on the other hand, usually means an unauthorized release of confidential data, whether intentional or unintentional by a third party but also an employee of a company.
Where can I check if my data has been breached?
Breachsense allows you to search across multiple data breaches, infostealer logs, and combo lists to see if your data has been breached. Use the Breachsense dark web scanner to see which of your organization’s accounts have been compromised.
How do you detect a data breach?
Detecting a data breach requires continuous monitoring across a broad range of sources, like the dark web, hacker forums, and ransomware channels, for compromised data. By tracking leaked credentials, stolen company data, and patterns of unusual activity, organizations can identify breaches early.
RECOMMENDED READING
Data Breach Types
Target Data Breach
Data Breach Search
Equifax Data Breach
Data Breach Causes
Data Breach Software
Cost of a Data Breach
What is a Data Breach
Data Breach Statistics
Company Data Breach
Data Breach Guidance
Data Breach Insurance
Data Breach Examples
Data Breach Response
Data Breach Mitigation
Data Breach Protection
Data Breach Prevention
Data Breach Notification
RECOMMENDED READING
Data Breach Compliance
Biggest Data Leak Cases
Home Depot Data Breach
Healthcare Data Breaches
Third Party Data Breaches
Breach Protection Platform
Data Breach Consequences
Data Security Best Practices
Data Breach Detection Tools
Data Breach Detection Software
Data Breach Response Checklist
Data Breaches Caused By Human Error
Impact of Data Breaches on Customers
Data Breaches Caused By Remote Work
Data Breaches Caused By Insider Threats
How to Prevent Healthcare Data Breaches
How to Create Breach Resistant Passwords
Consequences of a Data Breach in Healthcare
Data Breach Consequences on Small Businesses








